
Surveillance Exposure Scoring for Fintech: Inside DeepDiveData's V3 Model
As fintech adoption accelerates across emerging markets, mobile financial services are increasingly defined not only by functionality but by their privacy architecture. Many current privacy audits rely on permission counts, but these often miss how specific combinations of permissions multiply surveillance capability.
Over the last several months, we applied a structured Privacy Exposure Scoring Model (V3) across 24 Zimbabwean financial apps. This approach moved beyond simple permission counting and into deeper surveillance exposure modeling quantifying risk based on both:
- The sensitivity of each permission
- The co-occurrence bundles that enable surveillance-class data access
Surveillance-class access refers to permission combinations that enable continuous behavioral profiling, device-level identity reconstruction, and passive ambient data collection beyond stated app functions.
Let's walk through both the model and one real-world example.
Permission Sensitivity and Exposure Scoring - Technical Model (V3)
The V3 scoring model assigns exposure risk scores to each app based on both:
- Permission sensitivity weightings, and
- Risk escalation triggers for high-risk permission bundles.
This approach improves upon simple permission counting models by recognising that certain permissions represent inherently higher privacy exposure, and that particular combinations of permissions (co-occurrence bundles) enable advanced user profiling capabilities.
Step 1: Permission Weighting: Individual Sensitivity
Each permission type is assigned a base weight reflecting its relative sensitivity for identity profiling, behavioural tracking, and surveillance capability:
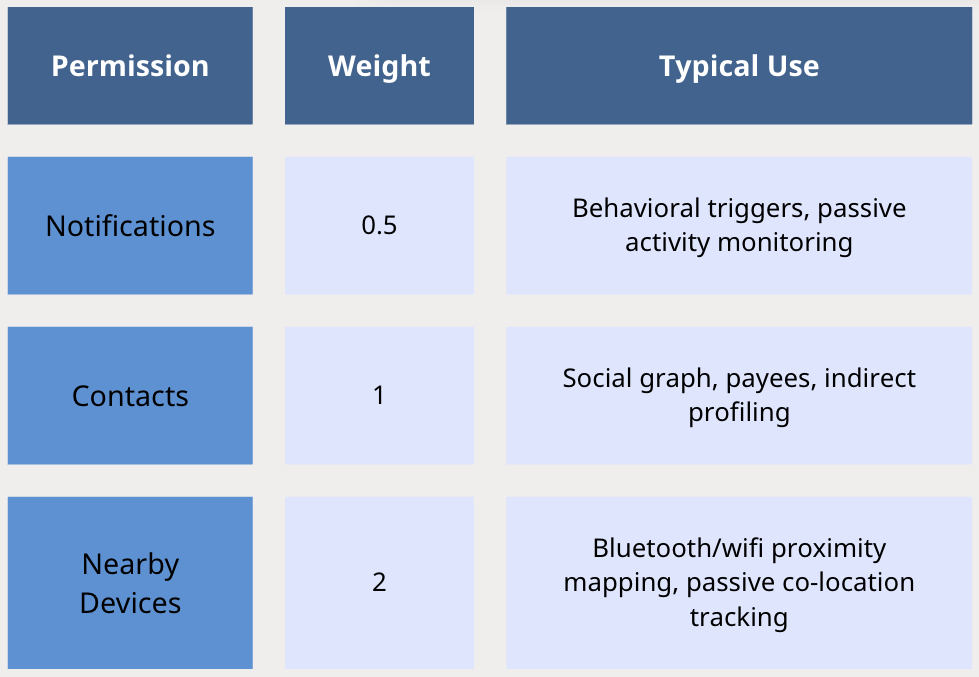
Step 2: Surveillance-Class Escalation Triggers
While individual permissions may serve legitimate functions (e.g., KYC onboarding), specific combinations enable exponential surveillance capability.
The model escalates an app's risk tier when both:
2.1 Condition 1 (Anchor Condition):
The app requests: ✅ Nearby Devices
This permission anchors the bundle trigger because it introduces passive device-to-device sensing and co-location risk.
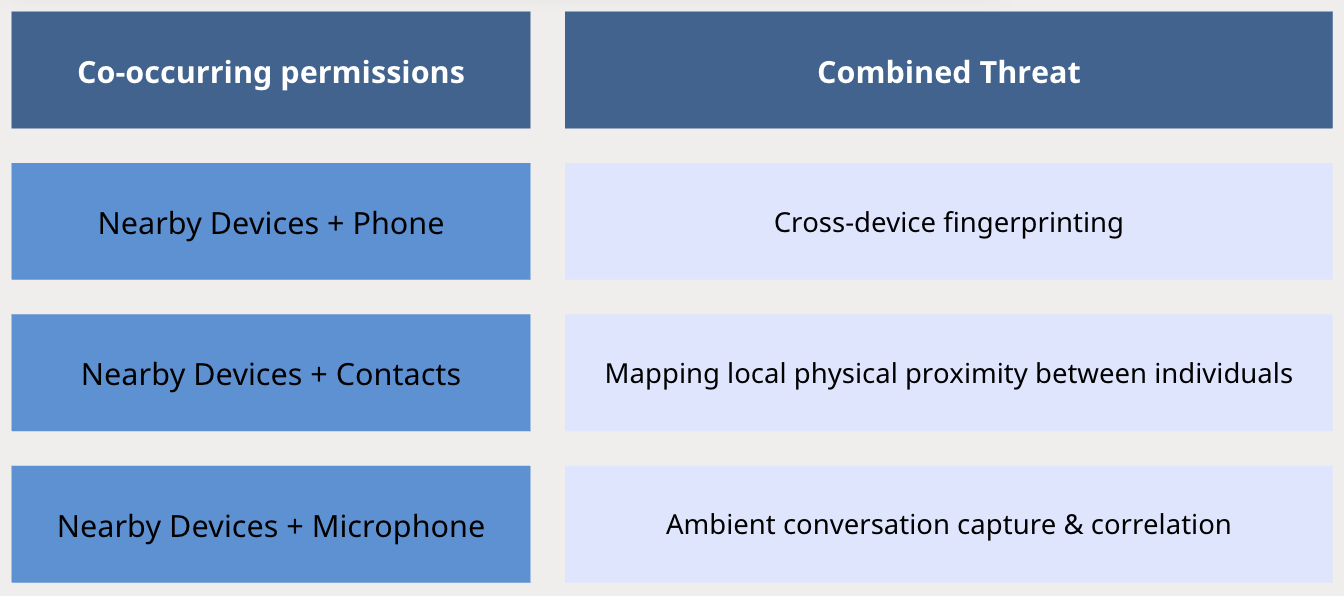
2.2 Condition 2 (Co-Occurrence Condition):
The app also declares at least 2 of the following permissions:
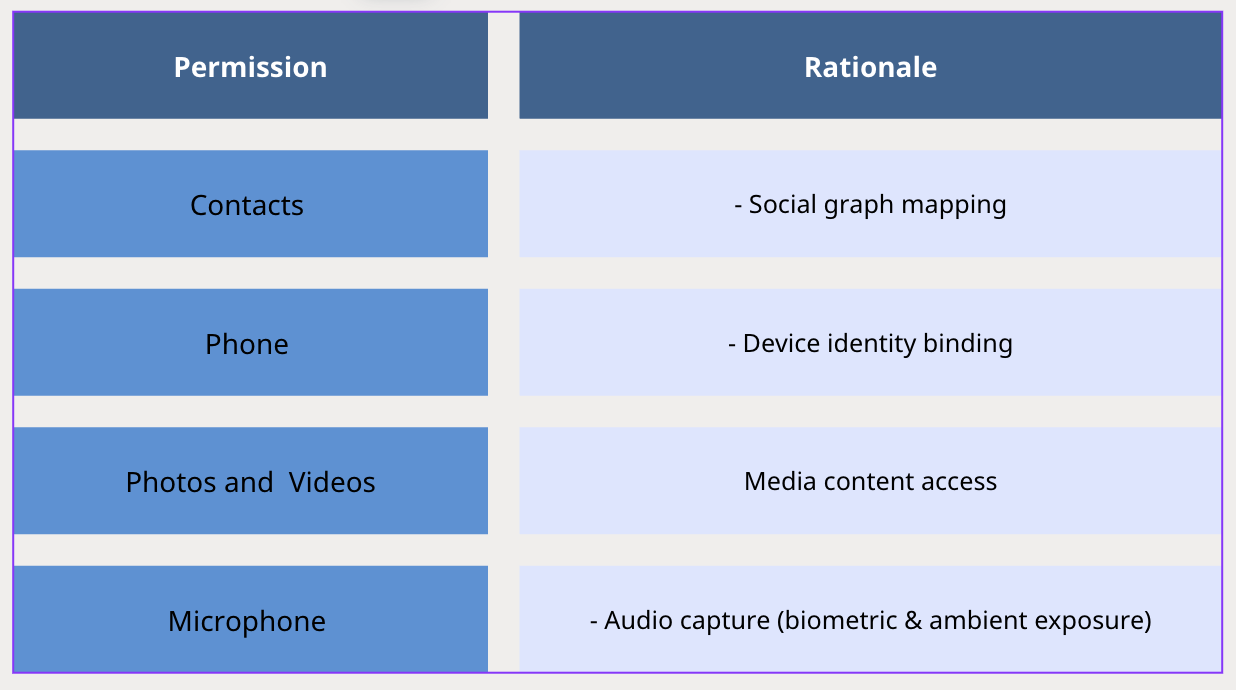
These co-occurrences enable:
- Passive ambient environment scanning
- Cross-device identity mapping
- Social graph reconstruction
- Behavioural tracking beyond explicit user consent
This escalation mechanism ensures that even well-intentioned fintech designs are properly flagged when device-level access converges.
Step 3: Tier Assignment Thresholds
The combined weighted score, plus any bundle escalation, drives final assignment into privacy exposure tiers:
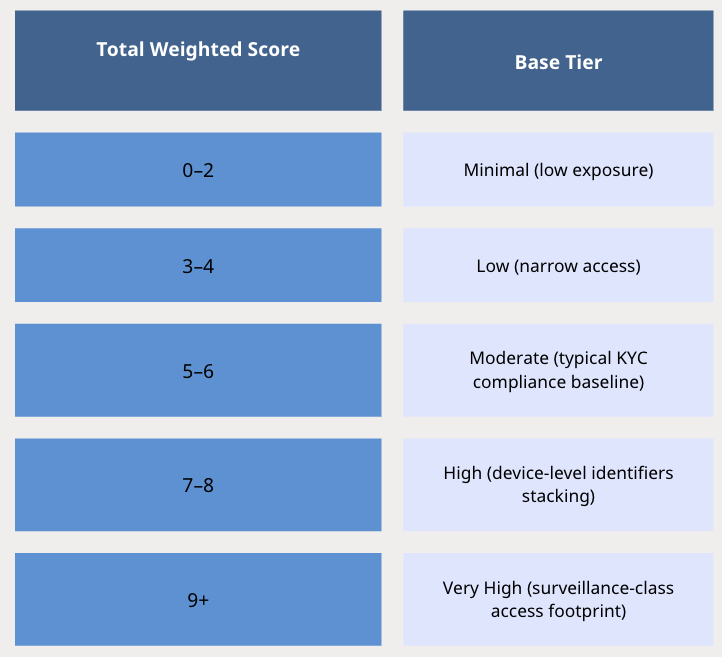
Example App Types and Scoring
Here's how different app types with expected declared permissions score with the V3 Model:
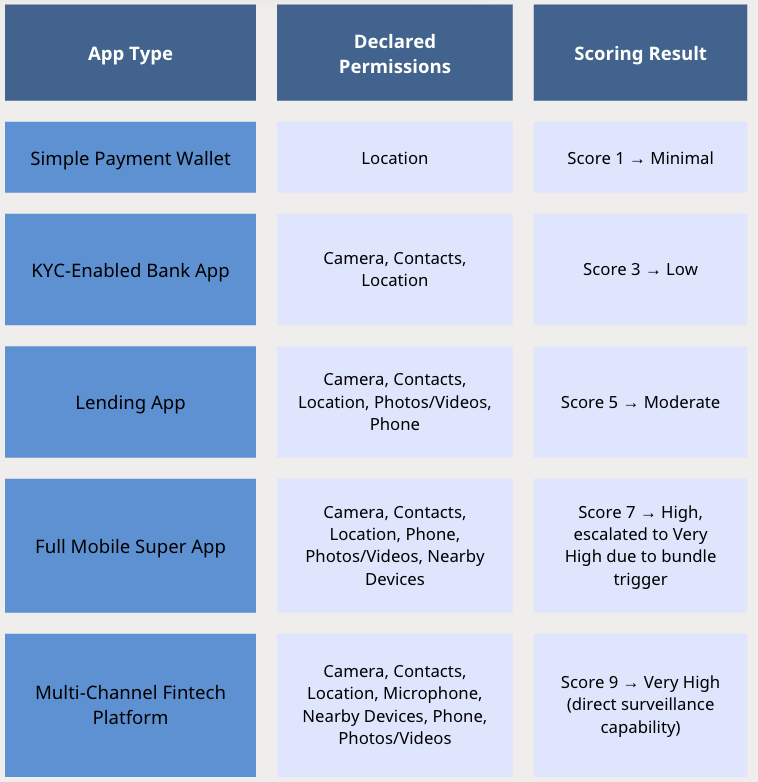
Case Study: InnBucks
Step 1️⃣: Declared Permissions
["Camera", "Contacts", "Location", "Nearby Devices", "Notifications", "Phone", "Photos and Videos"]
Step 2️⃣: Weighted Score
Permission (Weight)
- Camera (1)
- Contacts (1)
- Location (1)
- Nearby Devices (2)
- Notifications (0.5)
- Phone (1)
- Photos and Videos (1)
Total Weighted Score = 7.5 → Base Tier = High
Step 3️⃣: Escalation Check
Nearby Devices → ✅ Present
Co-occurring sensitive permissions:
Contacts ✅
Phone ✅
Photos and Videos ✅
🧮 Escalation triggered → Final Tier = Very High
This approach allows privacy auditors and regulators to differentiate between apps that simply request broad access and those that combine permissions to enable ongoing identity, behavioral, and device-level profiling. As mobile finance ecosystems mature, models like V3 will play a critical role in internal privacy audits, cross-border regulatory compliance, and establishing trust frameworks between fintech providers and infrastructure partners.
Full Dataset Available
This scoring model is part of our larger Zimbabwean Banking Apps & Data: Privacy Exposure Dataset for Zimbabwe, which includes:
- ✅ App-by-app permission matrices
- ✅ Full risk tier scoring
- ✅ Co-occurrence heatmaps
- ✅ Case study profiles
- ✅ Market entry compliance insights
👉 Get the full data pack here:
📄 Free Sample PDF: https://lnkd.in/d7kPiaPW
💳 Purchase Full Dataset (Instant Delivery): https://lnkd.in/dMz65m5d
(Delivery is automatically sent to the email used for payment.)